AKTU MCA I FCET NOTES UNIT III
UNIT III
----------
Unit III
Internet : Overview, Architecture, Functioning, Basic services like WWW, FTP,Telnet, Gopher etc., Search engines, E-mail, Web Browsers.
Internet of Things (IoT): Definition, Sensors, their types and features, Smart
The Internet is the global system of interconnected computer networks that uses the Internet protocol suite (TCP/IP) to communicate between networks and devices. It is a network of networks that consists of private, public, academic, business, and government networks of local to global scope, linked by a broad array of electronic, wireless, and optical networking technologies. The Internet carries a vast range of information resources and services, such as the inter-linked hypertext documents and applications of the World Wide Web (WWW), electronic mail, telephony, and file sharing.
Internet architecture
Functioning of internet
The internet is a global network of connected computers and servers that allows users to access and share information and resources from anywhere in the world. The basic functioning of the internet involves several interconnected layers of hardware and software that work together to transmit data between devices.
Here is a simplified overview of how the internet works:
Devices: The internet is accessed through various devices such as computers, smartphones, tablets, and servers that are connected to the network.
Protocols: The internet uses a set of standardized protocols, including TCP/IP (Transmission Control Protocol/Internet Protocol), to transmit and receive data packets between devices.
ISP: Internet Service Providers (ISPs) provide users with access to the internet by connecting their devices to the network via wired or wireless connections.
DNS: Domain Name System (DNS) servers translate human-readable domain names (such as www.google.com) into IP addresses (such as 172.217.5.78) that computers can understand.
Routing: When a user sends data over the internet, it is broken up into small packets and sent through a series of routers that determine the best path for the data to take to reach its destination.
Websites and servers: Websites and other online services are hosted on servers that are connected to the internet and provide users with access to content and resources.
Encryption: To ensure the security and privacy of data transmitted over the internet, encryption protocols such as SSL (Secure Sockets Layer) and TLS (Transport Layer Security) are used to encrypt data before it is transmitted and decrypt it when it is received.
Overall, the internet is a complex and constantly evolving network that requires the cooperation of many different devices and technologies to function effectively.
WWW
The World Wide Web (WWW) is a network of online content that is formatted in HTML and accessed via HTTP. The term refers to all the interlinked HTML pages that can be accessed over the Internet. The World Wide Web was originally designed in 1991 by Tim Berners-Lee while he was a contractor at CERN.
The World Wide Web is most often referred to simply as “the Web.”
The World Wide Web is what most people think of as the Internet. It is all the Web pages, pictures, videos and other online content that can be accessed via a Web browser. The Internet, in contrast, is the underlying network connection that allows us to send email and access the World Wide Web. The early Web was a collection of text-based sites hosted by organizations that were technically gifted enough to set up a Web server and learn HTML. It has continued to evolve since the original design, and it now includes interactive (social) media and user-generated content that requires little to no technical skills.
We owe the free Web to Berners-Lee and CERN’s decision to give away one of the greatest inventions of the century.
FTP
File Transfer Protocol (FTP) is a standard Internet protocol for transmitting files between computers on the Internet over TCP/IP connections. FTP is a client-server protocol where a client will ask for a file, and a local or remote server will provide it.
The end-users machine is typically called the local host machine, which is connected via the internet to the remote host—which is the second machine running the FTP software.
Anonymous FTP is a type of FTP that allows users to access files and other data without needing an ID or password. Some websites will allow visitors to use a guest ID or password- anonymous FTP allows this.
Although a lot of file transfer is now handled using HTTP, FTP is still commonly used to transfer files “behind the scenes” for other applications — e.g., hidden behind the user interfaces of banking, a service that helps build a website, such as Wix or SquareSpace, or other services. It is also used, via Web browsers, to download new applications.
How FTP works
FTP is a client-server protocol that relies on two communications channels between client and server: a command channel for controlling the conversation and a data channel for transmitting file content. Clients initiate conversations with servers by requesting to download a file. Using FTP, a client can upload, download, delete, rename, move and copy files on a server. A user typically needs to log on to the FTP server, although some servers make some or all of their content available without login, known as anonymous FTP.
FTP sessions work in passive or active modes. In active mode, after a client initiates a session via a command channel request, the server initiates a data connection back to the client and begins transferring data. In passive mode, the server instead uses the command channel to send the client the information it needs to open a data channel. Because passive mode has the client initiating all connections, it works well across firewalls and Network Address Translation (NAT) gateways.
How to FTP
Files can be transferred between two computers using FTP software. The user’s computer is called the local host machine and is connected to the Internet. The second machine, called the remote host, is also running FTP software and connected to the Internet.
- The local host machine connects to the remote host’s IP address.
- The user would enter a username/password (or use anonymous).
- FTP software may have a GUI, allowing users to drag and drop files between the remote and local host. If not, a series of FTP commandsare used to log in to the remote host and transfer files between the machines
Web Browsers
A web browser is a software program that allows a user to locate, access, and display web pages. In common usage, a web browser is usually shortened to “browser.” Browsers are used primarily for displaying and accessing websites on the internet, as well as other content created using languages such as Hypertext Markup Language (HTML) and Extensible Markup Language (XML).
Browsers translate web pages and websites delivered using Hypertext Transfer Protocol (HTTP) into human-readable content. They also have the ability to display other protocols and prefixes, such as secure HTTP (HTTPS), File Transfer Protocol (FTP), email handling (mailto:), and files (file:). In addition, most browsers also support external plug-ins required to display active content, such as in-page video, audio and game content.
A variety of web browsers are available with different features, and are designed to run on different operating systems. Common browsers include Internet Explorer from Microsoft, Firefox from Mozilla, Google Chrome, Safari from Apple, and Opera. All major browsers have mobile versions that are lightweight versions for accessing the web on mobile devices.
Web browsers date back to the late 1980s when an English scientist, Tim Berners-Lee, first developed the ideas that led to the World Wide Web (WWW). This consisted of a series of pages created using the HTML language and joined or linked together with pointers called hyperlinks. Following this was the need for a program that could access and display the HTML pages correctly – the browser.
In 1993, a new browser known as Mosaic was developed, which soon gained widespread usage due to its graphical-interface capability. Marc Andreesen, a member of the Mosaic development team, left in 1994 to develop his own commercial browser based on Mosaic. He called it Netscape Navigator and it quickly captured over 90 percent of the nascent browser market. It soon faced stiff competition in 1995 from Microsoft’s Internet Explorer, which was freely bundled with Windows 95 (and later versions of Windows). It was pointless to buy Navigator when Internet Explorer was free, and as a result, Navigator (and Netscape) were driven into the ground. But while Mosaic and Netscape are no longer around, the age of the browser was launched and continues to this day, as more and more applications move to the web.
Search Engines
Search engine is a service that allows Internet users to search for content via the World Wide Web (WWW). A user enters keywords or key phrases into a search engine and receives a list of Web content results in the form of websites, images, videos or other online data. The list of content returned via a search engine to a user is known as a search engine results page (SERP).
To simplify, think of a search engine as two components. First a spider/web crawler trolls the web for content that is added to the search engine’s index. Then, when a user queries a search engine, relevant results are returned based on the search engine’s algorithm. Early search engines were based largely on page content, but as websites learned to game the system, algorithms have become much more complex and search results returned can be based on literally hundreds of variables.
There used to be a significant number of search engines with significant market share. Currently, Google and Microsoft’s Bing control the vast majority of the market. (While Yahoo generates many queries, their back-end search technology is outsourced to Microsoft.)
E-Mail
E-mail (electronic mail) is the exchange of computer-stored messages by telecommunication. (Some publications spell it email; we prefer the currently more established spelling of e-mail.) E-mail messages are usually encoded in ASCII text. However, you can also send non-text files, such as graphic images and sound files, as attachments sent in binary streams. E-mail was one of the first uses of the Internet and is still the most popular use. A large percentage of the total traffic over the Internet is e-mail. E-mail can also be exchanged between online service provider users and in networks other than the Internet, both public and private.
E-mail can be distributed to lists of people as well as to individuals. A shared distribution list can be managed by using an e-mail reflector. Some mailing lists allow you to subscribe by sending a request to the mailing list administrator. A mailing list that is administered automatically is called a list server.
E-mail is one of the protocols included with the Transport Control Protocol/Internet Protocol (TCP/IP) suite of protocols. A popular protocol for sending e-mail is Simple Mail Transfer Protocol and a popular protocol for receiving it is POP3. Both Netscape and Microsoft include an e-mail utility with their Web browsers.
Gopher
Gopher is a client/server directory system that launched in 1991. It allowed people to quickly browse resources on the internet. When you used a Gopher client, you would see a hierarchical menu of links that either led to documents, telnet-based applications, FTP sites, or other Gopher servers.
The Gopher is a communication protocol designed for distributing, searching, and retrieving documents in Internet Protocol networks. The design of the Gopher protocol and user interface is menu-.driven, and presented an alternative to the World Wide Web .
Gopher is an Internet application that allows you to browse many different kinds of resources by looking at menus or listings of information available. Its function is easy to remember because of its name: you use Gopher to "go fer" information that is on other computers all over the world. The menus in the Gopher system allow you to see what information is there; the Gopher client on your system then brings the information you want to your computer screen. The Gopher servers of the world are all interconnected and have been compared to a large library full of resources.
You need to have a Gopher client running on your server to access and use this application. To find out if you have Gopher, either click on the Gopher icon or type "Gopher" at the command prompt. If your system is running a Gopher client, this will connect you to a root menu of resources from which you can proceed to browse the "libraries" of the world. The menus are constructed in a hierarchical order; to return from whence you came you simply need to type "u" for "up"--this takes you up to the next menu level. You can also just "quit" the application from whatever point you are. Some Gophers are text-based and others use icons (graphical representations) to lead from menu to menu.
If you find a site with interesting and useful information, you can mark it by using the bookmark function of the Gopher service. Then, the next time you log on, you can view your bookmarks and go directly to that useful site. All Gopher clients are different, so you need to check the documentation of the system you are using to know what command to use for bookmarks and other useful Gopher functions.
Below is the first screen of the FLTEACH gopher. This will give you an idea of what a gopher menu looks like. Moving the arrow to the item you want is the way to select and move through the layers of each menu.
IoT:
The Internet of Things (IoT) refers to a system of interrelated, internet-connected objects that are able to collect and transfer data over a wireless network without human intervention.
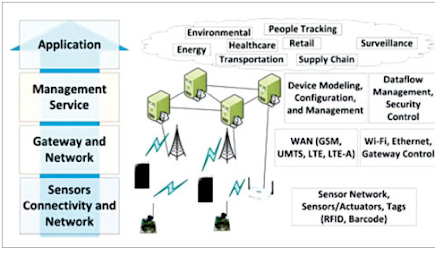
In an Internet of Things (IoT) ecosystem, two things are very important: the Internet and physical devices like sensors and actuators. As shown in Fig. 1, the bottom layer of the IoT system consists of sensor connectivity and network to collect information. This layer is an essential part of the IoT system and has network connectivity to the next layer, which is the gateway and network layer.
Sensors:
The main purpose of sensors is to collect data from the surrounding environment. Sensors, or ‘things’ of the IoT system, form the front end. These are connected directly or indirectly to IoT networks after signal conversion and processing. But all sensors are not the same and different IoT applications require different types of sensors. For instance, digital sensors are straightforward and easy to interface with a microcontroller using a Serial Peripheral Interface (SPI) bus. But for analog sensors, either analog-to-digital converter (ADC) or Sigma-Delta modulator is used to convert the data into SPI output.
Actuator:
An actuator is a device that produces a motion by converting energy and signals going into the system. The motion it produces can be either rotary or linear.
Features of sensors
Sensors are devices that detect or measure physical or chemical properties of the environment or other systems, and convert them into electrical signals that can be processed by electronic circuits. Some common features of sensors include:
Sensitivity: This refers to the ability of a sensor to detect changes in the measured parameter. A highly sensitive sensor can detect even small changes in the environment or system it is monitoring.
Range: The range of a sensor refers to the minimum and maximum values of the measured parameter that the sensor can detect accurately. For example, a temperature sensor may have a range of -40°C to 125°C.
Accuracy: This refers to how close the sensor's readings are to the true value of the measured parameter. A highly accurate sensor provides more reliable data than a less accurate one.
Precision: Precision refers to how consistently the sensor can measure the same value under the same conditions. A highly precise sensor will produce similar readings for the same measured parameter, while a less precise sensor may produce more variable readings.
Response time: This refers to how quickly a sensor can detect changes in the measured parameter and produce a signal. A faster response time may be important in certain applications, such as in process control systems.
Robustness: Robustness refers to the ability of a sensor to function accurately and reliably under different environmental conditions, such as temperature, humidity, and pressure.
Resolution: Resolution refers to the smallest change in the measured parameter that the sensor can detect. For example, a pressure sensor with a resolution of 0.1 kPa can detect changes as small as 0.1 kPa.
Linearity: This refers to how closely the sensor's output corresponds to changes in the measured parameter. A linear sensor produces a proportional output for proportional changes in the measured parameter, while a non-linear sensor may produce a non-proportional output.
Stability: Stability refers to how well a sensor maintains its accuracy and performance over time. A stable sensor will provide consistent and reliable readings over a long period of time.
Power consumption: This refers to the amount of electrical power that the sensor requires to operate. Low-power sensors may be important in applications where battery life is a concern.
Some common types of IoT sensors
Temperature sensors
These devices measure the amount of heat energy generated from an object or surrounding area. They find application in air-conditioners, refrigerators, and similar devices used for environmental control. They are also used in manufacturing processes, agriculture, and the health industry.
Temperature sensors can be used almost in every IoT environment, from manufacturing to agriculture. In manufacturing, sensors are used to monitor the temperature of machines. In agriculture, these can be used to monitor the temperature of the soil, water, and plants.
Temperature sensors include thermocouples, thermistors, resistor temperature detectors (RTDs) and integrated circuits (ICs)
Humidity sensors
The amount of water vapour in air, or humidity, can affect human comfort as well as many manufacturing processes in industries. So monitoring humidity level is important. Most commonly used units for humidity measurement are relative humidity (RH), dew/frost point (D/F PT) and parts per million (PPM).
Motion sensors
Motion sensors are not only used for security purposes but also in automatic door controls, automatic parking systems, automated sinks, automated toilet flushers, hand dryers, energy management systems, etc. You use these sensors in the IoT and monitor them from your smartphone or computer. HC-SR501 passive infrared (PIR) sensor is a popular motion sensor for hobby projects.
Gas sensors
These sensors are used to detect toxic gases. The sensing technologies most commonly used are electrochemical, photo-ionisation and semiconductor. With technical advancements and new specifications, there are a multitude of gas sensors available to help extend the wired and wireless connectivity deployed in IoT applications.
Smoke sensors
Smoke detectors have been in use in homes and industries for quite a long time. With the advent of the IoT, their application has become more convenient and user-friendly. Furthermore, adding a wireless connection to smoke detectors enables additional features that increase safety and convenience.
Pressure sensors
These sensors are used in IoT systems to monitor systems and devices that are driven by pressure signals. When the pressure range is beyond the threshold level, the device alerts the user about the problems that should be fixed. For example, BMP180 is a popular digital pressure sensor for use in mobile phones, PDAs, GPS navigation devices and outdoor equipment. Pressure sensors are also used in smart vehicles and aircrafts to determine force and altitude, respectively. In vehicle, tyre pressure monitoring system (TPMS) is used to alert the driver when tyre pressure is too low and could create unsafe driving conditions.
Image sensors
These sensors are found in digital cameras, medical imaging systems, night-vision equipment, thermal imaging devices, radars, sonars, media house and biometric systems. In the retail industry, these sensors are used to monitor customers visiting the store through IoT network. In offices and corporate buildings, they are used to monitor employees and various activities through IoT networks
IR sensors
An infrared (IR) sensor is an electronic device that measures and detects infrared radiation in its surrounding environment.
These sensors can measure the heat emitted by objects. They are used in various IoT projects including healthcare to monitor blood flow and blood pressure, smartphones to use as remote control and other functions, wearable devices to detect amount of light, thermometers to monitor temperature and blind-spot detection in vehicles.
Proximity sensors
These sensors detect the presence or absence of a nearby object without any physical contact. Different types of proximity sensors are inductive, capacitive, photoelectric, ultrasonic and magnetic. These are mostly used in object counters, process monitoring and control.
Smart Cities
Smart cities are urban areas that leverage technology and data to improve the quality of life of their citizens, enhance sustainability, and boost economic growth. They use sensors, data analytics, and other digital technologies to optimize the use of resources and services such as transportation, energy, waste management, and public safety.
Some examples of smart city initiatives include intelligent traffic management systems, energy-efficient buildings, connected public transport, smart waste management, and public Wi-Fi hotspots. By integrating technology into urban planning and management, smart cities aim to reduce costs, enhance efficiency, and create more livable and sustainable urban environments.
However, smart cities also face challenges such as privacy concerns, cybersecurity risks, and potential exclusion of those who may not have access to or be able to afford the necessary technology. Therefore, a balance between technological advancement and equitable access and inclusion must be achieved for smart cities to truly benefit all citizens.
What is the industrial internet of things (IIoT)?
The industrial internet of things (IIoT) refers to the extension and use of the internet of things (IoT) in industrial sectors and applications. With a strong focus on machine-to-machine (M2M) communication, big data, and machine learning, the IIoT enables industries and enterprises to have better efficiency and reliability in their operations. The IIoT encompasses industrial applications, including robotics, medical devices, and software-defined production processes.



0 Comments:
Post a Comment
Subscribe to Post Comments [Atom]
<< Home